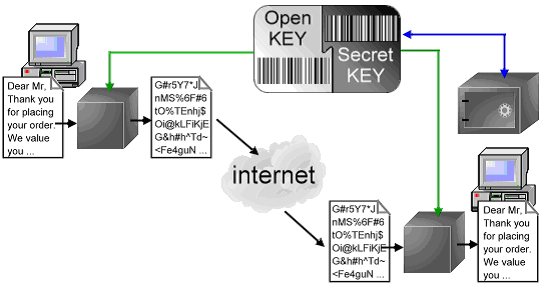
Information is coded with a key into ciphertext so it is unrecognizable until it is decoded with a key back into the original information.
When transfering private information over the web, the ciphertext is transfered, and then decoded when it reaches its destination (assuming the correct destination with an approprate key).
Between the years 100 and 44 BC Julius Caesar used a form of encryption to send message to trusted aquaintances. This is one of the earliest examples of encryption. He used the normal alphabet but shifted each letter by three. (Ex. A is replaced by D, B by E, etc) for government communications. This is very simple use of encryption, but at the time, this was creative and secret enough to succeed in its purpose.
Two encryption systems:

Asymmetric (PGP) - Information is coded using a session key. This session key is then coded using a public key that corresponds to the receiving computers private key. The private (or secret)key is used to decode the session key in order to decode the information. This is how emails are sent.